Now you can your subscriptions online anytime
your bills 24/7 securely without sign-in
to discuss your custom requirements
Click here to explore Infrastructure in the Middle East
We can manage your existing servers
Suitable for websites requiring security & high performance

Loading...

Loading...
Ideal for Ecommerce, High-traffic Websites, Web & Mobile Applications

Loading...

Loading...
Perfect for Internet Applications with custom configurations and SLAs
Website Firewall (WAF)
Cloud-based WAF that actively blocks malicious traffic.
Custom WAF Rules
Tailor the WAF settings to safeguard your particular application or website against cyber
threats. Based on your specified parameters, implement actions such as blocking or prompting verification for incoming requests.
OWASP Core Ruleset
Automatically incorporates the OWASP ModSecurity Core Rule Set to defend against the primary
vulnerabilities identified by the Open Web Application Security Project (OWASP).
Page Rules
Page Rules allow you to customize page / url functionality to match your unique needs.
Bot Mitigation
Secure your web forms and APIs against programmatic attacks. With Bot Manager high performance
bot rules use browser validation to detect malicious automated traffic and prevent it from reaching your web application.
Rate Limiting (IP-based)
Limit the number of requests a certain IP address can make, and prevent abuse from "repeat
offender" IP addresses.
IPv6, HTTP/2, SPDY
Support both IPv4 and IPv6 connections to your site without a single change to your existing
infrastructure. HTTP/2 brings advancements in efficiency, security, and speed, particularly on high-latency and mobile connections.
Header Rewrites
Rewrite headers helps to control header request and response.
Comment Spam Protection
Stop spammers from posting to your website.
Content Scraping Protection
Protect all of your content including text, images and email addresses from web scrapers.
Captcha/JS Challenge
Captcha served to visitors matching the triggered rules, and JS Challenge will run a JavaScript
challenge that validates whether the visitor is using a legitimate browser.
SSL Certificate
WebProtect provides you with default SSL and allows updating with your existing purchased SSL
Custom SSL Certificate
Customers can deploy their own SSL certificates for terminating SSL/TLS at the edge.
L3/L4 DDoS Protection
Protection against L3/L4 (network and transport layers of OSI model) distributed denial of
service (DDoS) attacks.
CDN
Data centers located across the globe provide visitors with location-based access to your
website, while removing latency and improving performance.
Cache TTL Expiry
Cache time before data is fetched from origin.
Load Balancing
Traffic splitting rules enable the distribution of site traffic among alternative origins.
Geo Based Load Balancing
Global Load Balancing ensures that visitors receive dynamic content from origin servers
closest to them.
Anycast DNS
Fast responsive times globally and nearinstant updates.
Malware Monitoring
Protect your brand’s reputation by knowing when your site is blocklisted and remove the
headache of getting it removed.
Security Vulnerbility/PCI Scans
Vulnerbility Scanning for over 1000 plus security checks.
Reporting
Intuitive dashboard with different reporting options.
Alerting
Configure alerts to be received by email on different conditions.
Standard Support
24*7 Support Availability, Multiple Support Channels, Unlimited Support Requests,Self Service Platform
Measured Response Time.
Malware Remediation
One time professional Service.
Managed Service
Ongoing management with 24/7 Multi-channel Priority Support & Faster Response Time. Managed WAF,
CDN, DNS, SSL, Malware Monitoring etc.
is delivered via email, making it the most common attack vector
(Verizon, 2019)A company lost 1.65M Dirhams due to the SQL Injection happened to their eCommerce website
We have implemented Web Security Solution for their eCommerce websites which protected the website from attacks through http/s including SQL Injection, Cross Sripting etc.
Protecting your website‘s security with a comprehensive approach, incorporating elements such as a Website Firewall (WAF), custom WAF rules, OWASP Core Ruleset, page rules, bot mitigation, rate limiting (IP-based), support for IPv6, HTTP/2, SPDY, header rewrites, comment spam protection, content scraping protection, Captcha/JS challenge, SSL certificate, custom SSL certificate, and L3/L4 DDoS protection ensures robust defense against a wide range of threats.
Enhance your website‘s performance with webProtect‘s advanced CDN capabilities, including optimized cache TTL expiry, load balancing for efficient resource distribution, geo-based load balancing for targeted content delivery, and Anycast DNS for lightning-fast response times across the globe.
Elevate your webProtect experience with comprehensive Monitoring & Analytics, featuring advanced capabilities such as continuous Malware Monitoring, thorough Security Vulnerability/PCI Scans, detailed Reporting, and real-time Alerting, ensuring proactive security and actionable insights for your online presence.
Benefit from top-tier Support & Services with webProtect, offering comprehensive Malware Remediation and expert Managed Service solutions, ensuring proactive protection and seamless management of your online security needs.
A Web Application Firewall (WAF) is a security tool that protects web applications from various cyber threats by monitoring and filtering incoming and outgoing traffic
An SSL Certificate is a digital certificate that encrypts communication between a user‘s browser and a website, ensuring secure transmission of sensitive information
DDoS Protection safeguards websites and networks by mitigating and deflecting distributed denial-of-service attacks, ensuring uninterrupted online availability
A Content Delivery Network (CDN) is a distributed network of servers that accelerates the delivery of web content to users, improving website performance and reliability
Load Balancing optimizes resource distribution across servers to ensure efficient performance and prevent overloads, enhancing system reliability
Anycast DNS enhances website reliability and speed by routing user requests to the nearest server location, minimizing latency
Malware Monitoring ensures constant surveillance for malicious software, safeguarding systems from potential threats
Vulnerability/PCI Scans identify weaknesses and ensure compliance with Payment Card Industry standards, enhancing overall security
is delivered via email, making it the most common attack vector
(Verizon, 2019)A company lost 1.65M Dirhams due to the SQL Injection happened to their eCommerce website
We have implemented Web Security Solution for their eCommerce websites which protected the website from attacks through http/s including SQL Injection, Cross Sripting etc.
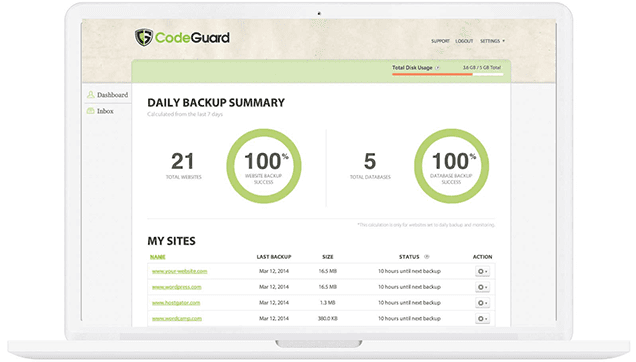
Utilizing sophisticated version control software, we provide incremental agent-less backups and 1-click restore option to reverse damage caused to your network of websites – with any mix of CMSs: WordPress, Joomla, Drupal – all in one place
With essential backup, malware remediation, and rollback capabilities we keep your site safe and secure
Your website is auto backed up everyday and it only saves changes or updates to your storage space
System automatically scans, discovers, and fixes viruses, trojans, rootkits, spyware, or other malware threats your website encounters
For WordPress websites we provide the ability to manage backups, plugins and themes from a single dashboard. Users can even restore their website directly from the WordPress dashboard
Built-in technology that automatically sends you an email if there are any additions, modifications or deletions between each version of your website of what has been modified
WebProtect adheres to industry best practices for data protection. All backups and passwords are encrypted, secure connections (SFTP/SSH/SSL) are used when possible, and annual vulnerability testing is performed by an independent agency. To date, WebProtect has not experienced any data breaches or successful hacks or attacks
Backups are stored on Amazon Web Services Simple Storage System, known as S3. S3 boasts object durability levels of 99.999999999%, achieved by storing redundant copies of data across multiple geographies and facilities. S3 is not the cheapest alternative for data storage, but it is one of the most reliable
Our data stored on Amazon Web Services (AWS) is stored utilizing Server Side Encryption (SSE). AWS handles key management and key protection for us, with one of the strongest block ciphers available, 256-bit Advanced Encryption Standard (AES-256)
Yes, you can connect directly to your MySQL database, usually through Port 3306, or via SSH tunneling using either your FTP credentials or separate credentials. Each time we retrieve database content, a mysqldump command is executed. Most MySQL databases are small enough that this process does not create a noticeable server load

For the initial backup, all file content is retrieved using the “get” command over FTP or SFTP. This process utilizes disk I/O as each file is transferred to our servers, while CPU and memory requirements remain minimal
Subsequent backups are differential, meaning only the changed content is transferred. This is done using the “ls – list” command to examine file metadata, including name, size, timestamp, file type, permissions, and last modified date. If any of these attributes have changed or if a new file has been added, the modified or new file is transferred to our servers. If a file has been deleted, we update our repository accordingly. Because only the changed file content is transferred, the majority of subsequent backups require minimal memory, CPU, and I/O resources
When a customer requests to restore a previous version of their website, it first examines the live site to identify its current content. This allows us to efficiently sync the differences to or from your site. For example, if a hack alters only your .htaccess file, it will replace the compromised file with a clean, older version instead of reloading the entire site
We deliver best-in-class cybersecurity solutions for your organization's data, endpoint, web, email protection to prevent intrusions and stay resilient 3 product navigation under plan

Browse tips, article & how-to guides made for 24/7 Self-Help
Cybersecurity threats are a significant concern for any organization, and they often prompt actions to protect sensitive information and maintain business continuity. Here are some common actions organizations take in response to cybersecurity threats:
Taking proactive and reactive measures to address cybersecurity threats helps protect your organization's data, reputation, and overall operational integrity.
To elevate cybersecurity in your company, you should adopt a multi-layered approach that combines advanced technologies, processes, and strategies. Here are steps to take your cybersecurity to the next level:
By taking these steps, you can significantly enhance your company’s cybersecurity posture and better protect against evolving threats.
Internal and external cyber threats are two distinct categories of security risks, each with its own characteristics and potential impacts. Here’s a breakdown of the differences:
Source:These threats originate from within the organization. They can come from employees, contractors, or other insiders who have access to the organization's systems and data.
Types:
Motivation:
Access: Insiders typically have authorized access to the organization’s systems and data, which can make detecting and mitigating their actions more challenging.
Detection and Prevention:
Source: These threats come from outside the organization and are typically carried out by cybercriminals, hackers, or adversarial entities with no legitimate access to the organization's systems.
Types:
Motivation:
Access: External threats do not have authorized access and typically exploit vulnerabilities or weaknesses in systems to gain entry.
Detection and Prevention:
In summary, internal threats come from within and can be intentional or accidental, while external threats originate outside the organization and often involve unauthorized attempts to compromise security. Both require different strategies and tools for detection, prevention, and response.
Data backup is a crucial component of a comprehensive cybersecurity strategy for several reasons:
Data Recovery from Attacks
Minimizing Downtime
Business Continuity: Quick access to backups allows for rapid recovery and minimizes operational downtime, helping to maintain business continuity during and after an attack.
Protection Against Human Error
Mitigating Hardware Failures
Hardware Malfunctions: Hard drive crashes, server failures, or other hardware issues can result in data loss. Regular backups ensure that data is not permanently lost due to hardware failure.
Compliance and Legal Requirements
Protecting Against Data Corruption
File Corruption: Data files can become corrupted due to software bugs or hardware issues. Backups allow you to restore uncorrupted versions of your data.
Disaster Recovery
Natural Disasters: In the event of natural disasters such as fires, floods, or earthquakes, having offsite or cloud backups ensures that data can be recovered even if physical infrastructure is damaged or destroyed.
Long-Term Data Preservation
Historical Records: Backups provide a historical record of data, which can be valuable for auditing, analyzing trends, or recovering information that is no longer available through active systems.
Business Resilience
Risk Management: Regular backups are part of a broader risk management strategy, enhancing overall business resilience and preparedness for unforeseen events.
Best Practices for Data Backup
In summary, data backups are essential for recovering from data loss, ensuring business continuity, complying with regulations, and maintaining overall cybersecurity resilience.